StructuredSources
Welcome to Structured Sources, your go-to resource for the latest insights and updates on office technology and IT services. Explore a diverse range of articles written by both our team AND industry experts, designed to keep you informed about the ever-evolving world of technology solutions for your workplace. Whether you’re looking for tips on optimizing your office’s IT infrastructure, staying up-to-date with cybersecurity trends, or learning about the latest productivity tools, we have you covered.
Blog
Copilot is bringing another productivity boost to Teams
Teams is getting some Copilot-powered updates that will boost your business’s productivity even further. Here we tell you all about it.
Blog
The hidden dangers of free VPNs: Are you at risk?
Free VPNs may seem tempting, but they could be exposing your data to cyber criminals. We tell you how to protect your business.
Read More →
Blog
Is this the ultimate browser for business?
There’s a new browser that keeps work and personal browsing totally separate. Here’s how it works and when it launches.
Read More →
Blog
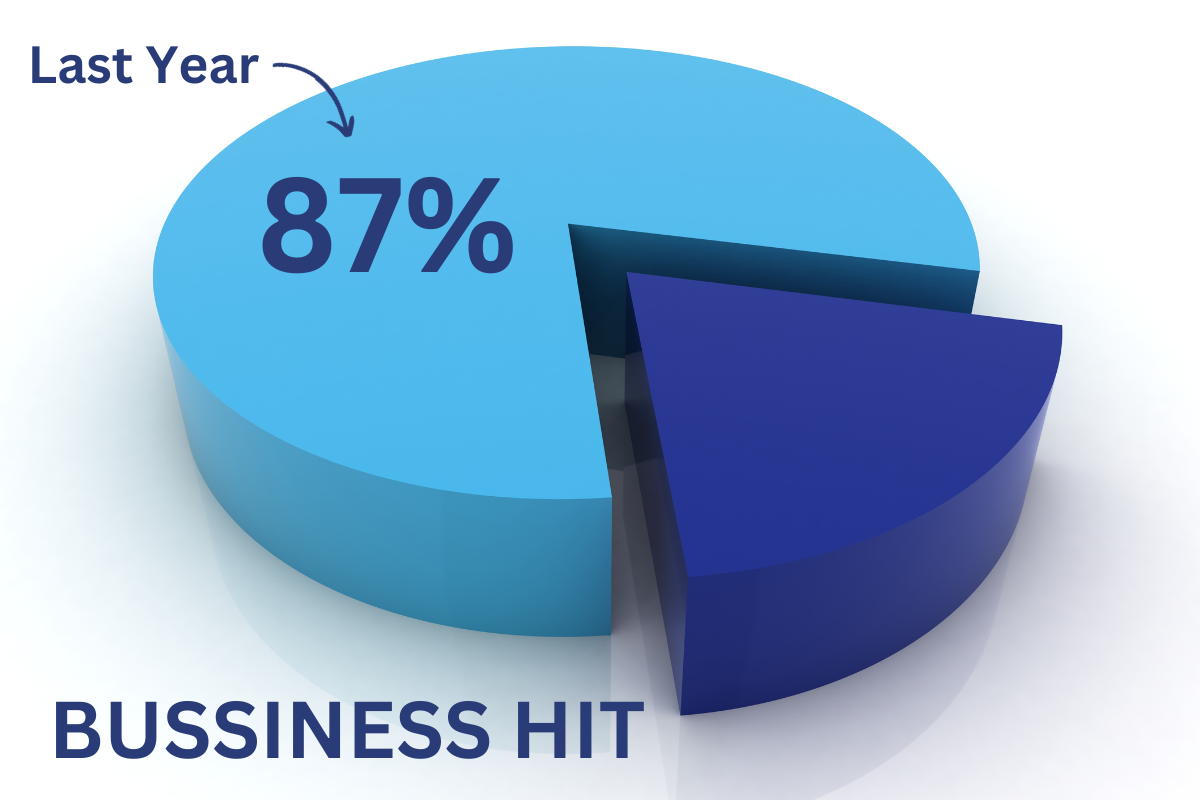
Scary stat: 87% of businesses hit by this in the last year
Cyber attacks aren’t reserved for big corporations. We show you how to protect your business from cyber criminals
Read More →
Blog
This is the latest trend in phishing attacks
Cyber criminals are using images embedded into emails. We’ll tell you how to protect your business from these new phishing scams.
Read More →
Blog
Privacy alert: Change this setting in Edge, now
There’s a setting in Edge that sends the images you view online to Microsoft. We give you all the details.
Read More →
Blog
Browse with confidence: Microsoft Edge’s security boost
We explain how Microsoft Edge is introducing some new security-boosting features to help you stay one step ahead.
Read More →
Blog
Now AI can make your Teams meetings more productive
Microsoft Teams Meeting Recap will summarize your meetings and even make a list of the action points. We show you its other benefits
Read More →
Blog
Stop! And think, before you act on that email
Don’t fall victim to cyber criminals. We explain what a BEC attack is and how to protect your business.
Read More →
Blog
Is your business data at risk? Don’t take chances with old tech
Old computers and external drives can put your sensitive business data at risk. We tell you how to dispose of them in the safest way ...
Read More →